Experienced, Personalized CyberSecurity Management
Experienced, Personalized CyberSecurity Management
Experienced, Personalized CyberSecurity ManagementExperienced, Personalized CyberSecurity ManagementExperienced, Personalized CyberSecurity ManagementExperienced, Personalized CyberSecurity Management
Experienced, Personalized CyberSecurity Management
Experienced, Personalized CyberSecurity ManagementExperienced, Personalized CyberSecurity ManagementExperienced, Personalized CyberSecurity ManagementNeed a Web Application Security Assessment?
Enterprise Security for SMBs
Our objective is to provide cybersecurity resources to small and medium sized businesses (SMBs) with goals of educating SMBs to the threat landscape as well as providing advisement or managed services to protect the business going forward.
Key Services
Vulnerability Management
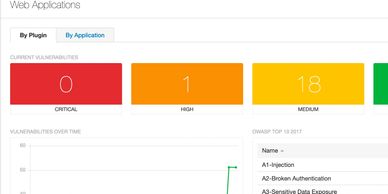
The processes and related technology defined by vulnerability management help organizations efficiently find and fix network security vulnerabilities.
Endpoint Security
Endpoint security is the process of securing the various endpoints within an organization, often defined as end-user devices such as mobile devices, laptops, and desktop PCs.
Cloud Security

Cloud security requires many of the same functionalities as traditional IT security: protecting critical information from theft, data leakage and deletion.
Web Sec Testing

Web application security testing is the process of testing, analyzing and reporting on the security level and/or posture of a Web application.
Penetration Testing
A penetration test is a simulated cyber attack against your computer system to identify any weak spots in your defenses which attackers could take advantage of.
Security Program
A security program is a documented set of your company's information security policies, procedures, guidelines, and standards.
Security Awareness Training
Let's Talk About Your Cybersecurity NEEDS!
Get started today!
Every business needs support, connectivity, and security. However, the specific needs of your business are unique to you. Send us a message, and we can help you find the services that best fit your needs.
Give us a call: 877-222-9643